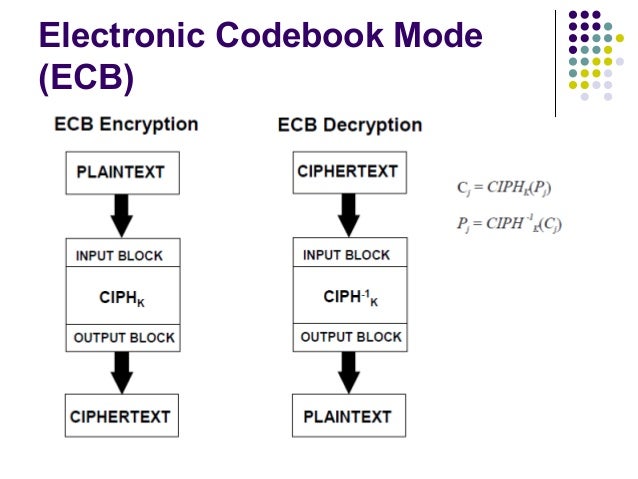
Is AES ECB mode useful for anything? What is counter mode encryption? Electronic codebook (ECB) ECB. Encryption parallelizable: Yes. Decryption parallelizable: Yes. Random read access: Yes.

In other words, the same plaintext value will always result in the same ciphertext value. The ECB mode is rather simple in realization. Limitations of ECB encryption scheme: 1. If blocks of the clear text are identical the corresponding blocks of ciphertext will be identical too. Otherwise if in the ciphertext some blocks are identical, the corresponding blocks of the clear text are identical too. The cryptanalyst can decipher only one of these blocks to find the contents of all of them.
In case the blocks are independent it becomes possible to replace some blocks of the ciphertext without knowledge of a key. The malefactor can replace part of blocks in the message with blocks intercepted during the previous message on the same key. In case of loss or insertion at least of one bit into ciphertext there will be a shift of bits and borders of block.
See full list on crypto. The most often use of this operating mode are those tasks where possibility of parallel processing is needed and there is no sequence of encryption of blocks of data (encrypting of a big database). Each of these blocks of a clear text is ciphered independently with use of the same key of enciphering of DES.
However, the ECB scheme is not recommended to encrypt. The header of such files i. ECB CTS) CipherText Stealing 2. CFB) Cipher Feed Back 5. BC) block chaining 4. It is the most basic form of block cipher encryption. CBC (Cipher Blocker Chaining) is an advanced form of block cipher encryption. With CBC mode encryption, each ciphertext block is dependent on all plaintext blocks processed up to that point.
Enter a passphrase (to generate a key) and a secret word. The secret word will then be ciphered with each. Lets start off with the basics of a block cipher encryption. In order to encrypt data, we need to have 2. We only discuss operation modes but there are more.
A good explanation about these modes can be found. The input plain text will be divided into blocks and each block will be encrypted with the key provided and hence identical plain text blocks are encrypted into identical cipher text blocks. The main idea is to split the clear text into blocks of N bits (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key. You have a cipher, that with a key will encrypt bytes of data. And you have some data, that is more than bytes.
So you have a problem. Well, ECB is the wrong solution to that probleyou just encrypt each 16-bytes block separately. Because this way blocks that were equal before encryption will remain equal also after!
And this will lead to all kinds of unwanted consequences. In fact, for a given key technically we can create a codebook of ciphertexts for all possible plaintext blocks. But with the issues of security, we don’t suggest to use this mode. The IV has the same size as the block that is encrypted.
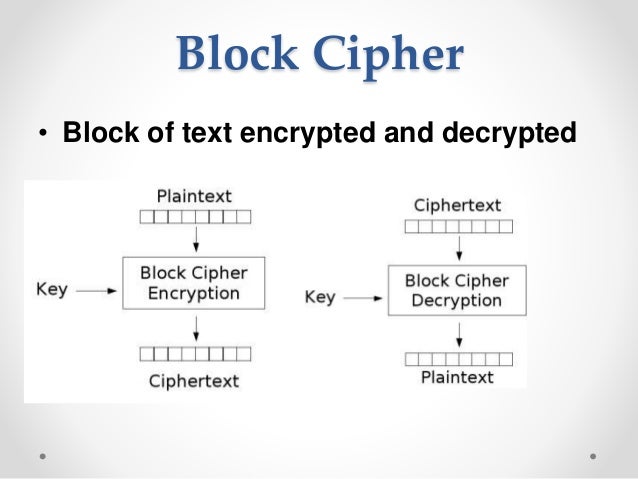
ECB (electronic code book) is basically raw cipher. For each block of input, you encrypt the block and get some output. For both methods, you just need a key and some data (must be of the type “bytes”) to encrypt, and pycrypto will do the job for you. Now, since AES is a block cipher, the data, IV (for CBC), and key have to be multiples of 16. Even a strong encryption algorithm used in ECB mode cannot blur efficiently the plaintext.
Only those who have the special key can decrypt it. AES uses symmetric key encryption , which involves the use of only one secret key to cipher and decipher information.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.